The workplace has transformed rapidly over the past ten years, as enterprises look to take advantage of the emerging technologies. Increasingly, employers and employees alike are able to leverage modern communications platforms and cloud technology to greatly enhance productivity and collaboration.
As adoption of internet-based solutions increases, however, so does cyber crime. Almost half of UK businesses suffered an attack in the past year, with many experiencing cyber security related issues at least once a week. Most employees are likely to have had some kind of security training, standard procedure for the majority of businesses now, but how many know exactly how hackers attack?
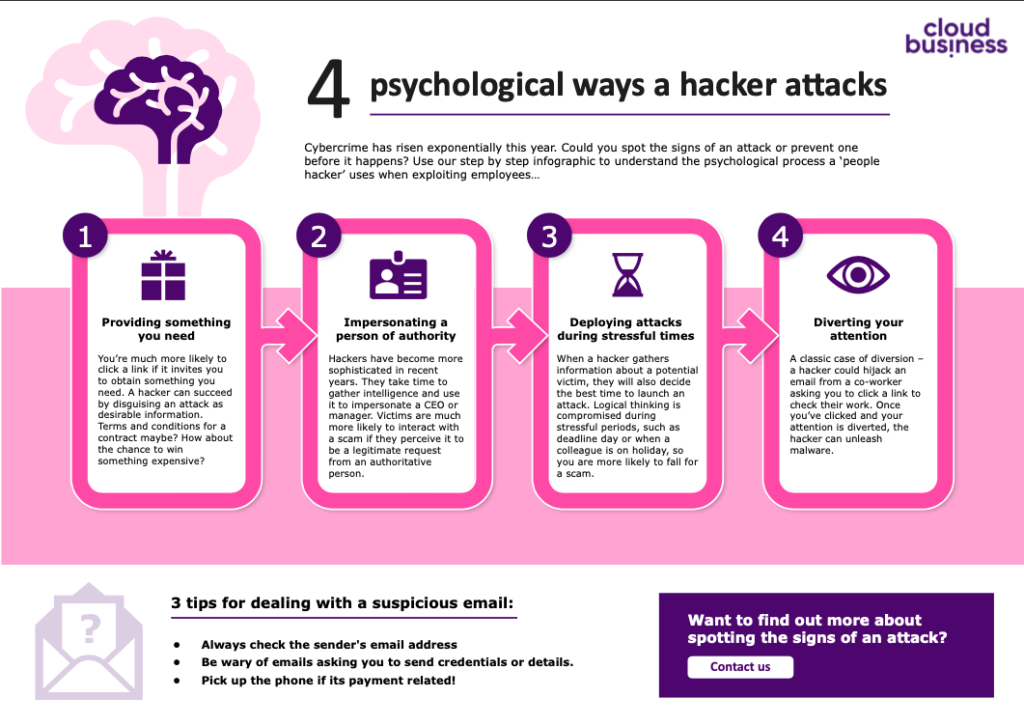
Psychological tricks hackers deploy
With more companies using strong security solutions, attackers are shifting focus to exploiting workers, rather than network and system vulnerabilities. These so-called ‘people hackers’ use four main techniques to bypass critical thinking. Understanding them can help you detect attacks before they do damage, reducing the risk of any human errors being made.
The most common psychological trick is quite simple: providing, or seeming to provide, something the victim needs. Many of us scoff at emails promising free products, but it can be much more crafty than that. Perhaps you’re at a conference when the Wi-Fi goes down. Before you know it, a backup network is up and running, but you’re prompted to enter your credentials again. This captive portal, purposefully launched by an attacker, could distribute malware or steal information from your device. The hacker has created the need and the solution, without arising suspicion.
Such attacks can be made more powerful if the attacker appears to be a person of authority. In recent years, there has been a rise in assailants that use information gathered about higher-level employees to impersonate them. From the victim’s perspective, it may look like their boss requesting an important document or credential. In reality, it could be an attacker posing as them. The further an attacker infiltrates a network, the easier such impersonation becomes.
Information gathering acquired through these methods also helps a hacker launch attacks during stressful periods, when logical thinking is compromised. When a deadline is looming and stress levels are high, employees are more likely to lose focus and download a document or open an attachment without thinking.
Finally, but crucially, hackers will try to divert your attention one way while performing an attack elsewhere. It could be as simple as an email from a “co-worker”, asking you to print and deliver a physical document to their desk, whilst your system is being compromised in the background.
Here’s a useful snapshot that you can share with colleagues and employees within your organisation:
Click on the infographic above to download a PDF you can share with your users.
Dealing with a suspicious email
Studies have revealed that around half of UK hacks are phishing scams via email. One in every 3,722 emails is a phishing attempt, and most of those make use of one or more of the psychological techniques above. With attackers getting more sophisticated, here’s how you can protect yourself properly:
Naturally, adhering to the above as well as staying productive during stressful times can be difficult, but thankfully, there are solutions out there that do most of the heavy lifting. Email security tools scan all inbound emails in real-time to look for suspicious content and detect anomalies in sender addresses or email headers. These alerts are passed on to employees in their email client while attachments are scanned before they can be downloaded. If a user does click a suspicious link, it will open in an isolated browser to protect from malware and phishing attempts.
Our partners LIBRAESVA have developed an insightful test to see how secure your organisation’s email is. Simply enter your email address and they will send you a series of test emails to see what gets through your email security.