Our step by step guide explains what’s happening, how to check if your tenant will be affected and how to disable basic authentication ahead of the deadline.
- What’s happening and when
- How to check if you’re using basic authentication
- How to disable basic authentication
Author: Ben Owens, Technical Architect at Cloud Business

An experienced Technical Architect, Ben supports customers with Professional Services. He takes a truly consultative approach by encouraging open and creative conversations about technology during the discovery phase, helping businesses to uncover the best solutions for their users.
Ben’s specialisms include Microsoft 365, Exchange, Identity and Modern Desktop with Microsoft Endpoint Manager.
Update, 12th October 2022
This article was originally published in August 2022, ahead of the October 2022 deadline.
We’ve seen a surge of interest in this blog post, as many businesses are not prepared for basic auth being disabled.
If you’re not ready, Microsoft have published two ways to delays this being disabled:
- Request that your tenant it’s opted out – this will delay basic authentication being disable until January 2023
- Re-enable basic authentication using a ‘one-time’ option in the tenant – again this will delay basic authentication being disable until January 2023
Microsoft plan to disable basic auth for Exchange Online in October 2022, what’s the background?
Basic authentication is essentially a login via username and password for client access. Importantly, basic auth doesn’t support multi-factor-authentication to verify logins and as a result is frequently used by attackers as a method to compromise user accounts.
Exchange Online has quite a lot of protocols which still allow basic authentication. To help close off these security gaps, Microsoft will be shutting these down from October 1st 2022. This will not be the switch-off date for everyone; Microsoft will randomly select tenants. They will send a 7-day warning into your Message Center posts and will then turn off basic authentication in your tenant. Microsoft plan to have this completed by the end of the year, so it’s important to be prepared.
Microsoft originally planned to have basic authentication disabled by October 2020, however due to the Covid-19 pandemic, the deadline was delayed by Microsoft to allow organisations more time to prepare. This time, basic authentication will be disabled and there won’t be any exceptions. In essence, you need to be ready for October 1st, 2022.
What does it mean? Once Microsoft disable basic authentication for your tenant, any users, applications, or services using basic auth will no longer be able to connect using that method.
So, are you using basic authentication for genuine reasons, and if so, where is it being used, by which account, and for what reasons? We’ve prepared a step by step guide to help you to prepare your business for this change.
How to check if you’re using basic authentication
A great way to determine if you’re using basic authentication in your tenant is by checking your Azure AD sign-in logs. Ask your administrator to check the following:
- Navigate to the Azure AD Sign In section here.
- Extend the default date from the past 24 hours, to 1 month. Depending on your level of licensing, you may only be able to extend this to 7 days. Note, that signing up to an Azure AD Premium trial will unlock 1 months’ worth of sign-in information.
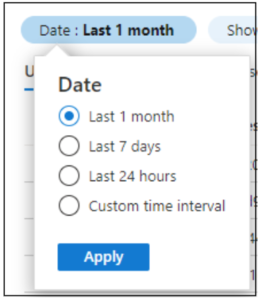
- From the filter drop down, select ‘Client App’ and ‘Apply’.
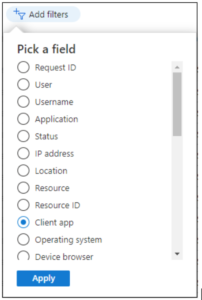
- From the ‘Client App’ client filter, there’s a long list of ‘Legacy Authentication Clients’. Select the following from the list:
- Autodiscover
- Exchange ActiveSync
- Exchange Online Powershell
- Exchange Web Services
- IMAP
- MAPI over HTTP
- Offline Address Book
- Other Clients
- Outlook Anywhere
- POP
- Reporting Web Services
- SMTP
- Universal Outlook
Note: that Microsoft are not turning off SMTP AUTH. Microsoft have turned off SMTP AUTH for millions of tenants who are not using it, but if SMTP AUTH is enabled in your tenant, it’s because Microsoft see usage and won’t touch it. Despite this, we recommend that you aim to remove all use of basic authentication unless it’s absolutely necessary.
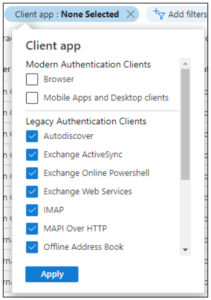
- Because we’re interested in the potential impact to the genuine uses of basic authentication, add the filter ‘Status’ and set it to ‘Success’.
- The results will provide a detailed breakdown of the sign-ins using basic authentication.
- You can choose to filter and navigate through the sign-in information in the Azure AD portal, or alternatively you can export the information into a CSV file and use Excel to filter the information:
Note: CSV download will be limited to 100,000 records, so if your query returns results past that limit, you may want to apply tighter filters by date/period or reduce the amount of ‘Client Apps’ selected in your filter.
What next?
If your query displays no results, then you’re looking good, and you could look to disable basic authentication before Microsoft does it for you in October.
However, if you have successful sign-in events listed, you may be wondering how to deal with them? The short answer is that ‘it depends’. However, here’s a guide to the common actions needed and guidance on the trickier actions needed:
Common Actions:
Outlook Client Version and Registry Keys – you may see references for connections to Exchange Online using MAPI, RPC, AutoDiscover and OAB. In these cases check the Outlook version number and check whether the relevant registry keys are in place to allow modern authentication – check here.
ActiveSync – many modern devices support ActiveSync connections using modern authentication. If those devices are attempting to connect using basic authentication, then it can be as simple as the user recreating the mail profile using their ActiveSync app, so it then uses modern authentication. Alternatively, I recommend you look at moving those users to the Outlook Mobile App instead.
POP/IMAP – connections into Exchange Online via POP/IMAP support modern authentication, however Microsoft Outlook doesn’t provide that connectivity. If you require that connectivity, then you’ll need to use an app which supports modern auth.
More Complex:
Devices, Applications and Services – Updating end user devices or advising users to use a different route of connection is relatively easy to progress, but the areas which can require more attention are applications, devices or services using basic auth. Identifying these may not be easy. This is because the connecting IP address may relate to a general internet breakout at one of your main locations. It may be using a generic service account, and the connection type may appear as nondescript. Try using a combination of the User Agent String, protocol, account name, IP address and time of authentication to help to determine its use.
Once you have a picture of what is connecting using basic auth, the next steps are determining the route to modern auth. Some applications or services may have a fairly easy way to switch over to modern auth, however some legacy systems may require an update to how they can authenticate.
How to disable basic authentication
To move ahead with blocking basic auth, you have two key steps:
Disabling Basic Auth via Conditional Access – if you’re licensed with Azure AD Premium P1 or above, you can create a conditional access policy to block legacy authentication. You can scope this out to users and groups. Focus on users who aren’t using basic auth first. As you progress in removing the need for basic auth, you can then expand the scope of your policy to other users. Note, that blocking legacy auth connections is carried out after verifying credentials. You ideally want to move to blocking basic auth via Authentication Policies.
Having basic authentication disabled via Authentication Policies – once you have removed the need for users, applications, or services to connect using basic auth, you can make basic authentication disabled using Authentication Policies. This is better than blocking legacy auth via Conditional Access as it’s done before credentials are verified.
Log Analytics
If you’re not already using it, we recommend setting up Azure AD log analytics. This provides you with a retention of sign-in and audit events and provides powerful workbooks which can help you understand current behaviours, risks and assists in assessing new Conditional Access policies and their potential impact.
Summary
The above provides direction of how to review and remove basic auth from your Microsoft 365 tenant.
If you’re looking for support in these areas, or are considering outsourcing your IT Support to a reliable team, get in contact and we’ll be happy to assist you.































