The cloud is a shared responsibility platform. This means that although most cloud technology companies provide excellent cloud security tools, it’s down to you to ensure that what you move to the cloud is secure.
Follow these 5 best practices to strengthen your cloud security:
- Identity and access control
- Security posture management
- Secure apps and data
- Threat protection
- Network security
Cloud security best practices
1: Identity and access control
Cloud security practice number one is to “assume breach”. This means behaving as if an attacker has breached the network perimeter and you need to do everything possible to protect your data and systems.
Identity and access control is where you can prevent attackers already instead your network perimeter from accesses the most sensitive data. Deploy the following:
Multifactor authentication – two or more of the following authentication methods
- Something you know (typically a password)
- Something you have (a trusted device that is not easily duplicated, like a phone)
- Something you are (biometrics)
Conditional access – set conditions that only allow sensitive resources to be accessed in certain way. For example, blocking or granting access depending on a specific location.
Operate a zero trust model – verify everything that wants to authenticate or connect to your IT environment. More on the zero trust model here >
2: Security posture management
Get ahead of the curve by prioritising and actioning recommendations to improve your security posture. This helps to get you out of reactive mode where you’re constantly responding to threats. If your IT environment is in 365 and Azure, a free Secure Score Analysis will help you understand what actions to prioritise.
3: Secure apps and data
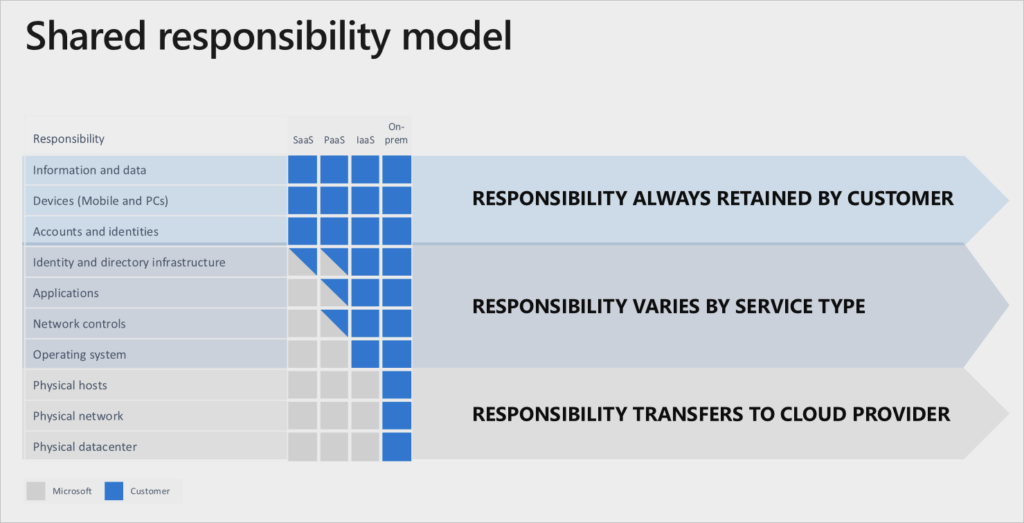
A layered, defense-in-depth strategy across identity, data, hosts, and networks protects your apps and data. Use encryption for data at rest and in transit, make sure your open dependencies don’t have vulnerabilities, and remember the cloud is a shared responsibility model (so you don’t have to do everything.)
Here’s what you’re responsible for, what’s shared and what’s down to your cloud provider:
4: Threat protection
Ensure threat detection is enabled for virtual machines, databases, storage, and IoT. Use a cloud provider that integrates threat intelligence, providing the necessary context, relevance, and prioritisation for you to make faster, better, and more proactive decisions. Consider a cloud-native security information and event management (SIEM) to scale with your needs.
5: Network security
You still need to protect your network perimeter but remember a firewall is only as good as the people who deploy and manage it! If you don’t have time to do this work consider a Managed Service that will do it for you. Protect online assets and networks from malicious traffic by deploying Distributed Denial of Service (DDoS) Protection. Use virtual networking, subnet provisioning, and IP addressing to create a micro-segmented network that is harder to penetrate.
If you need support strengthening your cloud security, get in touch for an informal chat about your IT environment.










