Everyone has witnessed the effects of an email hack, whether at work or at home. While your risk of being hacked may seem low, the threat to your company’s data is serious. Business email continues to be the primary security threat employers face-specifically, malicious email attachments, spear phishing and ransom ware.
So what exactly happens during the life cycle of an email hack, and how can you keep your company’s data safe? In the example below, a phishing attack uses email as the point of entry for network access. This can lead to malware installations, credential theft and much more.
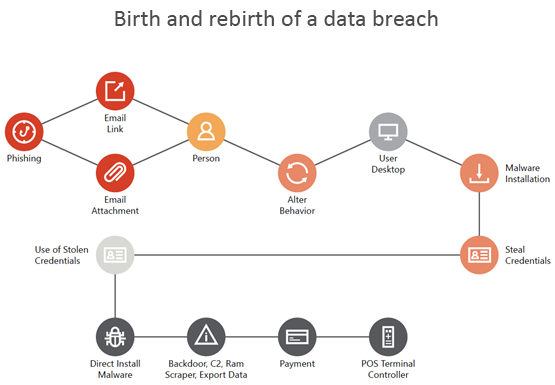
Defend against email threats with Exchange Online and Office 365
But what happens to a malicious email if you have advanced security protections in place? With Exchange Online and Office 365, suspicious attachments face multiple defenses before potentially landing in a user’s inbox. It also learns safe senders and allows you to customize preferences and specifically tailor them to your organization’s needs.
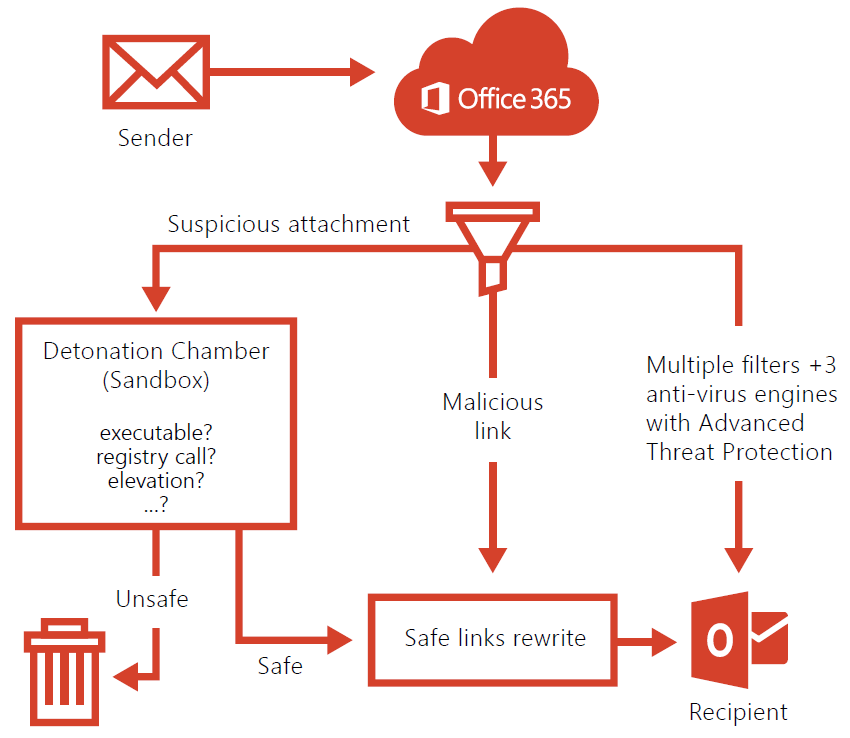
Suspicious emails and attachments go through multiple security checkpoints before making it to a user’s inbox
Read more: email migration is part of our digital transformation methodology.
While it is always advisable to stay on top of current trends and continue to learn about the types of threats you’ll be facing, the key to keeping company data safe is finding the right solution. Exchange online and Office 365 favours an integrated approach that combines attack protection, detection and response features to secure your organisation both now and in the future.
Thinking about Email migration? Check out our free migration consultation session to ensure your company is protected from data breach and other attacks.






